A) Configure the Cisco ESA to reset the TCP connection.
B) Configure policies to stop and reject communication.
C) Configure the Cisco ESA to drop the malicious emails.
D) Configure policies to quarantine malicious emails.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which Cisco command enables authentication, authorization, and accounting globally so that CoA is supported on the device?
A) aaa server radius dynamic-author
B) auth-type all
C) aaa new-model
D) ip device-tracking
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization received a large amount of SPAM messages over a short time period. In order to take action on the messages, it must be determined how harmful the messages are and this needs to happen dynamically. What must be configured to accomplish this?
A) Configure the Cisco WSA to modify policies based on the traffic seen.
B) Configure the Cisco ESA to modify policies based on the traffic seen.
C) Configure the Cisco WSA to receive real-time updates from Cisco Talos.
D) Configure the Cisco ESA to receive real-time updates from Cisco Talos.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which telemetry data captures variations seen within the flow, such as the packets TTL, IP/TCP flags, and payload length?
A) flow insight variation
B) software package variation
C) interpacket variation
D) process details variation
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the function of the Context Directory Agent?
A) reads the AD logs to map IP addresses to usernames
B) relays user authentication requests from Cisco WSA to AD
C) maintains users' group memberships
D) accepts user authentication requests on behalf of Cisco WSA for user identification
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
A) It allows the administrator to quarantine malicious files so that the application can function, just not maliciously.
B) It discovers and controls cloud apps that are connected to a company's corporate environment.
C) It deletes any application that does not belong in the network.
D) It sends the application information to an administrator to act on.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The company needs to be able to protect sensitive data throughout the full environment. Which tool should be used to accomplish this goal?
A) Cisco ISE
B) Web Security Appliance
C) Security Manager
D) Cloudlock
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
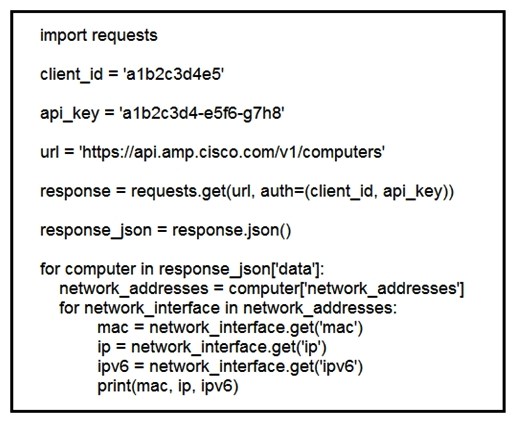 Refer to the exhibit. What does the API do when connected to a Cisco security appliance?
Refer to the exhibit. What does the API do when connected to a Cisco security appliance?
A) create an SNMP pull mechanism for managing AMP
B) gather network telemetry information from AMP for endpoints
C) get the process and PID information from the computers in the network
D) gather the network interface information about the computers AMP sees
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.)
A) Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
B) Cisco FTDv with one management interface and two traffic interfaces configured
C) Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
D) Cisco FTDv with two management interfaces and one traffic interface configured
E) Cisco FTDv configured in routed mode and IPv6 configured
G) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How many interfaces per bridge group does an ASA bridge group deployment support?
A) up to 16
B) up to 2
C) up to 4
D) up to 8
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which information is required when adding a device to Firepower Management Center?
A) username and password
B) encryption method
C) device serial number
D) registration key
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is a benefit of using Cisco FMC over Cisco ASDM?
A) Cisco FMC uses Java while Cisco ASDM uses HTML5.
B) Cisco FMC provides centralized management while Cisco ASDM does not.
C) Cisco FMC supports pushing configurations to devices while Cisco ASDM does not.
D) Cisco FMC supports all firewall products whereas Cisco ASDM only supports Cisco ASA devices.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which product allows Cisco FMC to push security intelligence observable to its sensors from other products?
A) Threat Intelligence Director
B) Encrypted Traffic Analytics.
C) Cognitive Threat Analytics.
D) Cisco Talos Intelligence
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is a characteristic of Cisco ASA NetFlow v9 Secure Event Logging?
A) It tracks flow-create, flow-teardown, and flow-denied events.
B) It provides stateless IP flow tracking that exports all records of a specific flow.
C) It tracks the flow continuously and provides updates every 10 seconds.
D) Its events match all traffic classes in parallel.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform?
A) Certificate Trust List
B) Endpoint Trust List
C) Enterprise Proxy Service
D) Secured Collaboration Proxy
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two.)
A) accounting
B) assurance
C) automation
D) authentication
E) encryption
G) D) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two.)
A) The Cisco WSA responds with its own IP address only if it is running in explicit mode.
B) The Cisco WSA is configured in a web browser only if it is running in transparent mode.
C) The Cisco WSA responds with its own IP address only if it is running in transparent mode.
D) The Cisco WSA uses a Layer 3 device to redirect traffic only if it is running in transparent mode.
E) When the Cisco WSA is running in transparent mode, it uses the WSA's own IP address as the HTTP request destination.
G) B) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the difference between Cross-site Scripting and SQL Injection attacks?
A) Cross-site Scripting is when executives in a corporation are attacked, whereas SQL Injection is when a database is manipulated.
B) Cross-site Scripting is an attack where code is executed from the server side, whereas SQL Injection is an attack where code is executed from the client side.
C) Cross-site Scripting is a brute force attack targeting remote sites, whereas SQL Injection is a social engineering attack.
D) Cross-site Scripting is an attack where code is injected into a database, whereas SQL Injection is an attack where code is injected into a browser.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is an attribute of the DevSecOps process?
A) security scanning and theoretical vulnerabilities
B) development security
C) isolated security team
D) mandated security controls and check lists
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which type of attack is social engineering?
A) trojan
B) MITM
C) phishing
D) malware
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Showing 181 - 200 of 213
Related Exams